Call a Specialist Today! 888-785-4402 | Free Shipping!
Cisco Secure DDoS Protection
Explore our flexible deployment options, award-winning service, and industry-leading service-level agreements (SLAs)
Note: For our full product catalog, please visit our Cisco Security focused site at SecureCloudGuard.com.
Cisco Secure DDoS Protection
Explore our flexible deployment options, award-winning service, and industry-leading service-level agreements (SLAs).

Secure Cloud DDoS available in Secure Choice EA
Secure DDoS protects the network and enhances resilience and availability under attack. Contact Cisco Security Sales today to add Cloud DDoS Protection to your Secure Choice Enterprise Agreement (EA).
Distributed Denial-of-Service (DDoS) attacks continue to become more frequent, more powerful, and more damaging. With the growing online availability of attack tools, the variants of possible attacks is now larger than ever.
Cisco DDoS protection solutions defend organizations against today’s most sophisticated DDoS attacks using advanced behavioral-based and machine learning algorithms to rapidly detect and mitigate both network-layer (L3/4) and application-layer (L7) attacks. Cisco DDoS mitigation solutions protect against encrypted SSL-based DDoS attacks without adding latency and use automatic, adaptive real-time protection to defend against zero-day attacks. Multiple deployment options, including cloud-based, CPE, and hybrid deployment options, offer solutions for every customer.
Secure DDoS Protection Video
Learn how Cisco Secure DDoS Protection enhances business resilience, protects the network, and ensures availability under attack.
Why Cisco Secure DDoS Protection?
In today's digital economy, your online business must be available 24x7x365 to customers, partners, and employees.

Zero-day DDoS protection
Adaptive, behavioral-based algorithms block never-before-seen attacks with the lowest false positive rate in the industry.

Highest availability under attack
Accurately distinguishes legitimate from malicious traffic, enabling advanced SLA and increasing service availability.

Data center efficiency
Comprehensive protection eliminates anomalous flows that consume network resources and impact application availability.
The first stop in protecting your edge
Choose the DDoS Protection coverage that suits you best.
Cloud DDoS
On-demand, always-on, or hybrid? We give organizations the widest security coverage from today's DDoS attacks.
Flexible deployment options
On-premises
Protects against application layer attacks. Limited protection against volumetric attacks.
- Behavioral real-time detection and mitigation
- Deploy
- Inline
- Out-of-path
- Smart tap
- Scrubbing center
- SSL mitigation
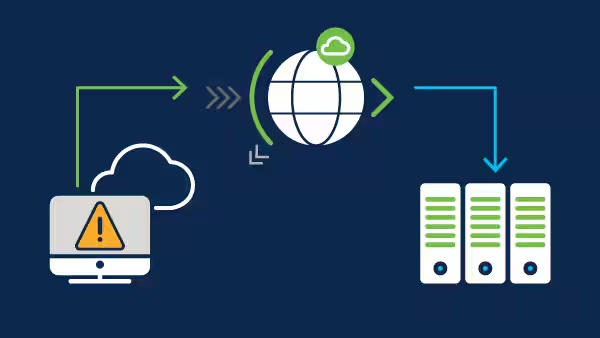
Always-on
Best solution for customers that are at high risk of attacks and/or very sensitive to downtime.
- Traffic always routed through Radware’s scrubbing center
- Real-time attack detection and mitigation
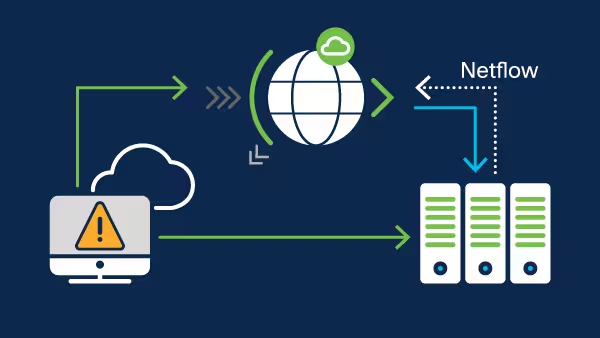
On-demand
Good for customers who have not yet been attacked and can tolerate brief outages.
- DDoS detection based on:
- NetFlow statistics
- Arbor TMS messages
- AWS and Azure telemetry
- Traffic diverted only in case of volumetric attacks
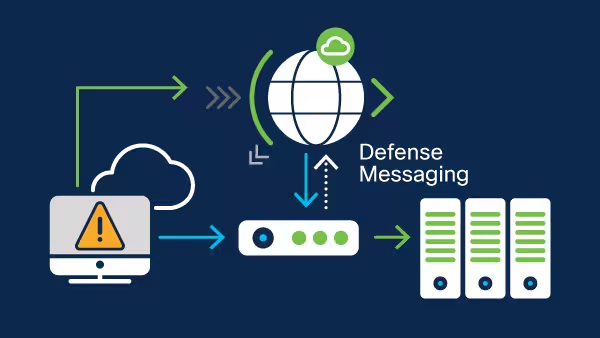
Hybrid
Best overall solution for protection against application layer and volumetric attacks.
- ntegrated: On-premises mitigation appliances with on-demand cloud protection
- Real-time detection and mitigation
- Traffic diverted to cloud upon pipe saturation

DDoS protection with the SecureX advantage
Unlock more value with the built-in Cisco SecureX. Our integrated platform unifies visibility, enables automation, and strengthens your security across network, endpoints, cloud, and applications.
WAFs protect websites from application vulnerability exploits like SQL injection, cross-site scripting (XSS), cross-site request forgery, session hijacking, and other web attacks. WAFs typically feature basic bot mitigation capabilities that block bots based only on IPs and fingerprinting.
Unfortunately, most WAFs often fall short when facing advanced, automated threats. Sophisticated next-gen bots mimic human behavior and often go undetected, abusing open-source tools or generating multiple violations in different sessions.
Against today’s sophisticated threats, standard WAF solutions just don’t get the job done.
| Security Capability | Bot Manager | Traditional WAFS | WAF + Bot |
|---|---|---|---|
| Protection from simple bots | Yes | Yes | Yes |
| Fingerprinting of malicious devices | Yes | Yes | Yes |
| Mitigation of dynamic IP and headless browser attacks | Yes | Limited | Yes |
| Detection of sophisticated bot attacks | Yes | No | Yes |
| Risk of blocking legitimate users (false positives) | Very low | High | Very Low |
| Collective bot intelligence (IPs, fingerprints, behavioral patterns) | Yes | No | Yes |
| Customized actions against suspicious bot types | Yes | No | Yes |
| Protection for OWASP Top 10 vulnerabilities | No | Yes | Yes |
| Protection from API vulnerabilities | Limited | Yes | Yes |
| Protection for Layer 7 denial of service (DoS) | Limited | Yes | Yes |
| HTTP traffic inspection | No | Yes | Yes |
| Masking of sensitive data | No | Yes | Yes |
| Compliance with HIPAA, PCI | Limited | Yes | Yes |
| Integration with DevOps | No | Yes | Yes |
| Blocking of malicious sources at the network level – access control list (ACL) | No | Yes | Yes |
Cisco makes the packaging data available for informational purposes only. It may not reflect the most current legal developments, and Cisco does not represent, warrant, or guarantee that it is complete, accurate, or up to date. This information is subject to change without notice.