Overview:
Viruses and other malicious code can overwhelm your IT resources disrupting business operations and impacting business transactions. The onslaught of spyware and unwanted Internet content can seriously impact employee productivity and expose individuals to identity theft. Providing comprehensive malware protection and content control, the Cisco ASA 5500 Series Content Security Edition allows enterprises to make full use of the Internet without the risk and costs associated with infections and threats impacting client systems. Combining enterprise-grade firewall and high-quality malware protection, the Cisco ASA 5500 Series Content Security Edition delivers a powerful all-in-one solution that provides strong protection and control for business network communications, stops network threats including viruses, worms, spyware, spam and phishing, and controls unwanted mail and Web content while reducing the operational costs and complexity of deploying and managing multiple point solutions.

Challenge
In today's marketplace, businesses rely on the Internet for their productivity, efficiency, customer interaction, and financial success. At the same time, the Internet has become a source of network threats from benign to severe, including viruses, spyware, phishing, and other malicious threats. Once a teenager vandal's playground, it has transitioned into a world of opportunity for cyber-criminals and organized crime where the motivation is monetary where it was once driven by fame and notoriety.
Businesses strive to maximize business continuity and security, increase employee productivity and reduce network wastage, control information theft and legal liabilities, and reduce operational expenses and management burden. Most businesses find it difficult to attain these business goals with a steady stream of Internet threats targeting client systems. Historically, balancing business demands with security requirements has meant adding more devices and technology-and more costs and complexity-to the network.
Solution:
The Cisco ASA 5500 Series Content Security Edition enables businesses to take advantage of the benefits of Internet business while providing you with a comprehensive gateway security and VPN connectivity solution. With its integrated firewall, content security, and VPN capabilities, the Cisco ASA 5500 Series Content Security Edition removes malware, spyware, spam, and phishing attempts from e-mail and Internet traffic, helping to ensure maximum business continuity and security. Combined with integrated URL filtering, which enables organizations to control employee Internet use by restricting access to unwanted Websites, the Cisco ASA 5500 Series Content Security Edition provides flexible, comprehensive perimeter security and employee productivity management. And with the inclusion of VPN services in the same solution, threat-protected remote access is also possible.
- Most trusted and deployed firewall technology-Building on the market-proven capabilities of the Cisco PIX Family of security appliances, the Cisco ASA 5500 Series allows valid business traffic to flow, while keeping out unwelcome visitors. And with its application control capabilities, the solution can limit peer-to-peer, instant messaging and malicious traffic, which can lead to security leaks, and the introduction of threats to the network.
- Market-leading content security capabilities-In the Cisco ASA 5500 Series, award-winning gateway security technology from Trend Micro is integrated with Cisco threat prevention capabilities, providing a comprehensive malware protection solution against spyware, viruses, spam, and inappropriate content with integrated URL and content filtering.
- Antivirus and anti-spyware-Using Trend Micro's award-winning antivirus and anti-spyware technology, Cisco ASA 5500 Series appliances can prevent virtually all known malicious code from crossing the Internet edge. This helps prevent the disruption of business-critical applications and services, and reduces the costly process of cleaning up after an infection.
- URL and content filtering, anti-phishing-Integrated URL filtering, content filtering, and anti-phishing technology helps protect the business as well as individual employees from the theft of confidential information, and helps reduce potential legal liabilities. It can also help businesses comply with regulations such as Health Insurance Portability and Accountability Act (HIPAA), Sarbanes-Oxley (SOX) and the Data Protection Act.
- Anti-spam-Integrated anti-spam technology removes most unsolicited e-mail before it hits the mail server, increasing employee productivity and preventing wastage of network bandwidth and storage.
- Threat-protected VPN-Building upon the market-proven VPN capabilities of the Cisco VPN 3000 Series Concentrator, the Cisco ASA 5500 Series Content Security Edition provides secure site-to-site and remote-user access to corporate networks and services. This solution offers businesses maximum flexibility for secure connectivity by combining support for Secure Sockets Layer (SSL) and IP Security (IPSec) VPN capabilities into a single, best-in-class solution. Using the services offered by the Cisco ASA 5500 Series Content Security Edition, businesses can enforce identity-based security and networking policies, as well as prevent malware and many other forms of attack, while extending their network securely to employees, contractors, and business partners.
- Easy deployment and management-The centralized management and monitoring suite enables large-scale deployment and operation of the Cisco ASA 5500 Series Content Security Edition with minimal staff and operational expenses. Cisco provides a complete solution covering management and monitoring. Also included with the solution is the Cisco Adaptive Security Device Manager (ASDM), which provides a powerful, yet easy-to-use browser-based management and monitoring interface for an individual device.
Business Benefits:
The Cisco ASA 5500 Series Content Security Edition provides the security and connectivity that helps your business with:
- Business Continuity-Prevents disruptions of business critical applications and services due to malware infections and security breaches
- Damage Cleanup-Reduces the costly process of cleaning up after an infection. Free up IT support resources from the costly process of cleaning up spyware, viruses, and other malware
- Employee Productivity-Increases employee productivity due to reduction of spam, spyware, and related distractions
- Network Resources-Prevents wastage of network bandwidth and storage by removing non-business relevant traffic and content.
The Cisco ASA 5500 Series Content Security Edition is the fulcrum of a complete solution for Internet edge security. Tight integration with Cisco management and monitoring systems enables organizations to deploy and maintain a security solution that enables the network and employees to deliver maximum value (Figure 1).
Figure 1. Solution Architecture
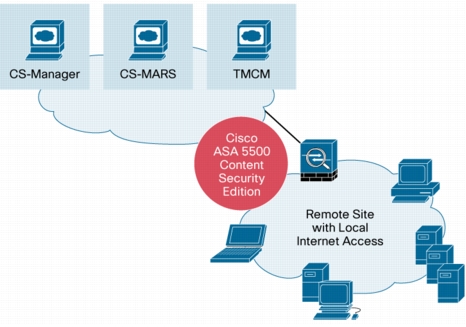
Primary Components
Cisco ASA 5500 Series Content Security Edition
Provides comprehensive client security at the edges of the network and remote site locations.
Management
Cisco Security Manager (CS-Manager) provides an enterprise-grade management infrastructure for large-scale deployments of Cisco security technologies.
Monitoring
Cisco Security Monitoring, Analysis, and Response System (CS-MARS) provides real-time monitoring and incident response capabilities, which enables organizations to get the most value from the advanced inspection services of the Cisco ASA 5500 Series Content Security Edition.
Complementary Solutions:
The Cisco ASA 5500 Series Adaptive Security Appliance is a modular platform that provides the next generation of security and VPN services for small and medium-sized business and enterprise applications. The comprehensive portfolio of services within the Cisco ASA 5500 Series enables customization for location-specific needs through its four tailored package product editions: the Firewall, IPS, Content Security, and VPN Editions.
These packages enable superior protection by providing the right services for the right location. At the same time, they enable standardization on the Cisco ASA 5500 Series platform to reduce costs in management, training, and sparing. Finally, each Edition simplifies design and deployment by providing pre-packaged location-specific security solutions.
Figure 2. Complementary Solutions

Cisco Systems and its partners offer world-class service and support tailored for your business. Cisco has adopted a lifecycle approach to services that addresses the necessary set of requirements for deploying and operating Cisco ASA 5500 Series security appliances. This approach can help you improve your network's business value and return on investment.